Submission to VIJ 2024-10-01
Keywords
- Cybersecurity, Online Banking Security, Threat Detection, Cyber Threats, Network Vulnerabilities, Authentication Security, Two-Factor Authentication (2FA), Risk Management, Data Encryption, Firewall Security.
Copyright (c) 2024 FNU Jimmy

This work is licensed under a Creative Commons Attribution 4.0 International License.
Abstract
The rapid expansion of online banking has introduced significant convenience and accessibility for consumers and financial institutions alike. However, it also brings a substantial increase in cybersecurity threats, making online banking systems prime targets for cybercriminals. This paper provides a comprehensive examination of the prevalent cybersecurity threats that online banking faces, including phishing attacks, malware, ransomware, man-in-the-middle (MITM) attacks, insider threats, and distributed denial-of-service (DDoS) attacks. We analyze these threats in-depth, exploring how each tactic is deployed to compromise security and exploit vulnerabilities within online banking systems.
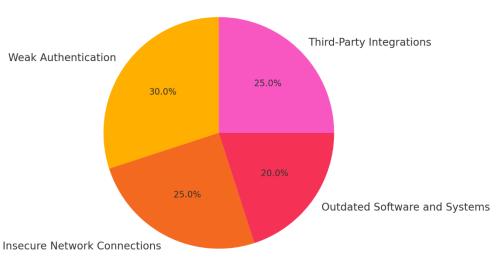
Moreover, this paper discusses specific vulnerabilities that exist in online banking platforms, such as weak authentication practices, insecure network connections, outdated software, and risks associated with third-party integrations. Through tables and graphical data, the paper offers a clear overview of the most common vulnerabilities and their prevalence, providing insights into how these weak points are exploited in the cyber landscape.
The impact of such cybersecurity breaches on financial institutions is also considered, highlighting the consequences that follow a security breach, such as financial losses, reputational damage, regulatory fines, and customer distrust. The findings reveal that these impacts not only affect individual financial institutions but can also undermine public confidence in digital banking as a whole.
Finally, the paper proposes several strategic defenses against these threats. Solutions include multi-factor authentication, end-to-end encryption, robust threat monitoring, regular security audits, and customer education initiatives, among others. Statistical data on the effectiveness of these strategies demonstrates their role in mitigating cyber risks and fortifying online banking systems against future attacks. This study concludes by emphasizing the critical need for continuous innovation in cybersecurity practices, as cyber threats continue to evolve in sophistication.
References
- Ghelani, D., Hua, T. K., & Koduru, S. K. R. (2022). Cyber security threats, vulnerabilities, and security solutions models in banking. Authorea Preprints.
- Uddin, M. H., Ali, M. H., & Hassan, M. K. (2020). Cybersecurity hazards and financial system vulnerability: a synthesis of literature. Risk Management, 22(4), 239-309.
- Stanikzai, A. Q., & Shah, M. A. (2021, December). Evaluation of cyber security threats in banking systems. In 2021 IEEE Symposium Series on Computational Intelligence (SSCI) (pp. 1-4). IEEE.
- Al-Alawi, A. I., & Al-Bassam, M. S. A. (2020). The significance of cybersecurity system in helping managing risk in banking and financial sector. Journal of Xidian University, 14(7), 1523-1536.
- Aslan, Ö., Aktuğ, S. S., Ozkan-Okay, M., Yilmaz, A. A., & Akin, E. (2023). A comprehensive review of cyber security vulnerabilities, threats, attacks, and solutions. Electronics, 12(6), 1333.
- Panja, B., Fattaleh, D., Mercado, M., Robinson, A., & Meharia, P. (2013, May). Cybersecurity in banking and financial sector: Security analysis of a mobile banking application. In 2013 international conference on collaboration technologies and systems (CTS) (pp. 397-403). IEEE.
- Mannan, M., & Van Oorschot, P. C. (2008, July). Security and usability: the gap in real-world online banking. In Proceedings of the 2007 Workshop on New Security Paradigms (pp. 1-14).
- Dawodu, S. O., Omotosho, A., Akindote, O. J., Adegbite, A. O., & Ewuga, S. K. (2023). Cybersecurity risk assessment in banking: methodologies and best practices. Computer Science & IT Research Journal, 4(3), 220-243.
- Gulyas, O., & Kiss, G. (2022, May). Cybersecurity threats in the banking sector. In 2022 8th International Conference on Control, Decision and Information Technologies (CoDIT) (Vol. 1, pp. 1070-1075). IEEE.
- Darem, A. A., Alhashmi, A. A., Alkhaldi, T. M., Alashjaee, A. M., Alanazi, S. M., & Ebad, S. A. (2023). Cyber threats classifications and countermeasures in banking and financial sector. IEEE Access, 11, 125138-125158.
- Shulha, O., Yanenkova, I., Kuzub, M., Muda, I., & Nazarenko, V. (2022). Banking information resource cybersecurity system modeling. Journal of Open Innovation: Technology, Market, and Complexity, 8(2), 80.
- Khabibullaev, T. (2024). Navigating the Ethical, Organizational, and Societal Impacts of Generative AI: Balancing Innovation with Responsibility. Zenodo. https://doi.org/10.5281/zenodo.13995243
- Ozkaya, E., & Aslaner, M. (2019). Hands-On Cybersecurity for Finance: Identify vulnerabilities and secure your financial services from security breaches. Packt Publishing Ltd.
- Hassan, A. O., Ewuga, S. K., Abdul, A. A., Abrahams, T. O., Oladeinde, M., & Dawodu, S. O. (2024). Cybersecurity in banking: a global perspective with a focus on Nigerian practices. Computer Science & IT Research Journal, 5(1), 41-59.
- JOSHI, D., SAYED, F., BERI, J., & PAL, R. (2021). An efficient supervised machine learning model approach for forecasting of renewable energy to tackle climate change. Int J Comp Sci Eng Inform Technol Res, 11, 25-32.
- Ghelani, H. (2024). AI-Driven Quality Control in PCB Manufacturing: Enhancing Production Efficiency and Precision. Valley International Journal Digital Library, 1549-1564.
- Joshi, D., Sayed, F., Saraf, A., Sutaria, A., & Karamchandani, S. (2021). Elements of Nature Optimized into Smart Energy Grids using Machine Learning. Design Engineering, 1886-1892.
- Ghelani, H. (2024). Advanced AI Technologies for Defect Prevention and Yield Optimization in PCB Manufacturing. Valley International Journal Digital Library, 26534-26550.
- Joshi, D., Parikh, A., Mangla, R., Sayed, F., & Karamchandani, S. H. (2021). AI Based Nose for Trace of Churn in Assessment of Captive Customers. Turkish Online Journal of Qualitative Inquiry, 12(6).
- Khambaty, A., Joshi, D., Sayed, F., Pinto, K., & Karamchandani, S. (2022, January). Delve into the Realms with 3D Forms: Visualization System Aid Design in an IOT-Driven World. In Proceedings of International Conference on Wireless Communication: ICWiCom 2021 (pp. 335-343). Singapore: Springer Nature Singapore.
- Mammadzada, A. Evolving Environmental Immigration Policies Through Technological Solutions: A Focused Analysis of Japan and Canada in the Context of COVID-19.
- Khambati, A. (2021). Innovative Smart Water Management System Using Artificial Intelligence. Turkish Journal of Computer and Mathematics Education (TURCOMAT), 12(3), 4726-4734.
- Priya, M. M., Makutam, V., Javid, S. M. A. M., & Safwan, M. AN OVERVIEW ON CLINICAL DATA MANAGEMENT AND ROLE OF PHARM. D IN CLINICAL DATA MANAGEMENT.
- Wu, D. (2024). The effects of data preprocessing on probability of default model fairness. arXiv preprint arXiv:2408.15452.
- Varagani, S., RS, M. S., Anuvidya, R., Kondru, S., Pandey, Y., Yadav, R., & Arvind, K. D. (2024). A comparative study on assessment of safety and efficacy of Diclofenac, Naproxen and Etoricoxib in reducing pain in osteoarthritis patients-An observational study. Int. J. Curr. Res. Med. Sci, 10(8), 31-38.
- Wu, D. (2024). Bitcoin ETF: Opportunities and risk. arXiv preprint arXiv:2409.00270.
- Viswakanth, M. (2018). WORLD JOURNAL OF PHARMACY AND PHARMACEUTICAL SCIENCES
- Singh, J. (2022). Deepfakes: The Threat to Data Authenticity and Public Trust in the Age of AI-Driven Manipulation of Visual and Audio Content. Journal of AI-Assisted Scientific Discovery, 2(1), 428-467.
- Singh, J. (2022). The Ethics of Data Ownership in Autonomous Driving: Navigating Legal, Privacy, and Decision-Making Challenges in a Fully Automated Transport System. Australian Journal of Machine Learning Research & Applications, 2(1), 324-366.
- Sharma, P., & Devgan, M. (2012). Virtual device context-Securing with scalability and cost reduction. IEEE Potentials, 31(6), 35-37.