Influence of Organizational Security Learning Practices on Insider Security Threats in SoCs in Kenya
Submission to VIJ 2024-08-05
Keywords
- Insider Threats, organizational security learning practices, observational learning, imitation and modelling, reinforcement learning and self-efficacy.
Copyright (c) 2024 Charles Mwenda Ikiara, Dr. Boniface Ratemo, Dr. George Musumba

This work is licensed under a Creative Commons Attribution 4.0 International License.
Abstract
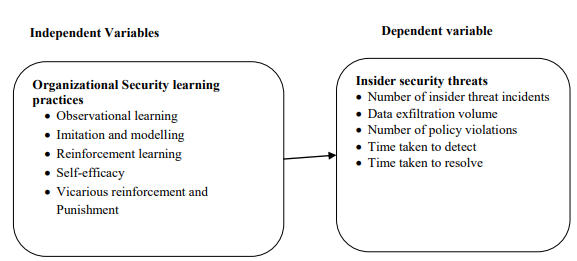
Insider threats have consistently been identified as key threats to State-owned Corporations and governments (SoCs). Research has shown that huge amounts of resources go towards safeguarding organizations’ assets and information systems from external threats in total disregard of potential threats from malicious and compromised insiders. Recent studies indicate that insider threats are on the rise and have cost the Kenyan economy $ 36Million USD. In addition, investigations show that these threats are increasing in scale, scope, and sophistication. The general objective of the study was to investigate on the organizational factors influencing insider security threats in State-owned Corporations in Kenya. Specifically, the study evaluated the influence of organizational security policies, organizational security learning practices and organizational communication practices on insider security threats in State-owned Corporations in Kenya. The study was anchored on the CISA Insider Threats Risk Score Model, deterrence theory, social learning theory and the communication privacy management theory. The study adopted descriptive correlational research design. The target population was 187 State-owned Corporations in Kenya. A census sampling design was used targeting the Security managers or their equivalent in SoCs. The researcher utilized a self-administered questionnaire as the data collection method. Data was analysed through quantitative techniques using the SPSS. The study established that organizational security policies have significant influence on insider security threats in SoCs in Kenya. The study also established that organizational security learning practices have significant influence on insider security threats in SoCs in Kenya. In addition, the study revealed that organizational communication practices have significant influence on insider security threats in SoCs in Kenya. The study also deduced that the combined influence of organizational security policies, learning practices and communication practices (organizational factors) significantly influence insider security threats in SoCs in Kenya. The study recommends that SoCs consider conducting a comprehensive review of their existing security policies, ensuring clarity on the severity of consequences for insider threats. Further, the study recommends that SoCs work on strengthening their learning policies to emphasize the importance of observational learning, role modeling, and positive reinforcement in the context of security awareness to address insider security threats. Additionally, the study recommends that SoCs provide training programs that emphasize effective communication practices surrounding privacy management.
References
- Al-Shanfari, I., Yassin, W., & Abdullah, R. (2020). Identify of Factors Affecting Information Security Awareness and Weight Analysis Process. International Journal of Engineering and Advanced Technology (IJEAT), 9(3), 534-42.
- Alsowail, R., & Al-Shehari, T. (2020). Empirical Detection Techniques of Insider Threat Incidents. IEEE Access, 1-1.
- Baykara, M., & Das, R. (2019). A novel honeypot-based security approach for real-time intrusion detection and prevention systems. Journal of Information Security and Applications, 41, 103-116.
- Bell, C., Rogers, M., & Pearce, M. (2019). The insider threat : Behavioral indicators and factors influencing likelihood of intervention. International Journal of Critical Infrastructure Protection, 24, 166-176.
- Chattopadhyay, P., Wang, L., & Tan, Y. (2018). Scenario-based insider threat detection from cyber activities. IEEE Transactions on Computational Social Systems, 5(3), 660-675.
- Cooley, G. C. (2021). Insider Threats' Behaviors and Data Security Management Strategies. Minneapolis, Minnesota: Walden Dissertations and Doctoral Studies.
- Dhillon, B. (2018). Insider security awareness training: A guide for security professionals. Boca Raton, Florida, United States: CRC Press.
- Gathu, K. (2020). Insider Threat Detection Model For Organizations: A Case Study Of Manufacturing Companies In Thika. Nairobi: Unpublished Masters in Information Systems and Technology thesis, United States International University-Africa.
- Haidar, D., & Gaber, M. M. (2019). Data stream clustering for real-time anomaly detection: an application to insider threats. Clustering Methods for Big Data Analytics, 115-144.
- Homoliak, I., Toffalini, F., Guarnizo, J., Elovici, Y., & Ochoa, M. (2019). Insight into insiders and it: A survey of insiderthreat taxonomies, analysis, modeling, and countermeasures. ACM Comput. Surv., 12, 101–117.
- Kisutsa, C., & Shiyayo, B. (2020). The kenya cyber security report. Nairobi: Communications Authority of Kenya.
- Liu, L., de Vel, O., Han, Q., Zhang, J., & Xiang, Y. (2018). Detecting and preventing cyber insider threats: A survey. IEEE Commun. Surv. Tutor, 20, 1397–1417.
- Maalem, A., Caulkins, B., Mohapatra, R., & Kumar, M. (2020). Review and insight on the behavioral aspects of cybersecurity. Journal of Cybersecurity, 3, 1-18.
- Myeongki, J., & Hangjung, Z. (2021). Preventing insider threats to enhance organizational security: The role of opportunity-reducing techniques. Telematics and Informatics, 63, 1-15.
- Ndeda, L. A., & Odoyo, C. O. (2019). Cyber threats and cyber security in the Kenyan business context.
- Pieterse, H. (2021). The cyber threat landscape in South Africa: A 10-year review. The African Journal of Information and Communication, 28, 1-21.
- Rodbert, M. (2020). Why organisational readiness is vital in the fight against insider threats. Network Security, 8(8), 7-9.
- Schoenherr, J., & Thomson, R. (2021). The cybersecurity (CSEC) questionnaire : Individual differences in unintentional insider threat behaviours. Journal of Information Security and Applications, 4, 8-28.
- Silaule, C., Makhubele, L., & Mamorobela, S. (2022). A model to reduce insider cybersecurity threats in a South African telecommunications company. South African Journal of Information Management, 24(1),1-8.
- Spear, B., Beyer, B. A., Cittadini, L., & Saltonstall, M. (2018). Changing mechanisms of enterprise security (comparing beyond corp with prevalent network security mechanisms). International Journal of Engineering & Technology, 7(3), 72-81.
- Torto, S., & Fernandez, F. (2022). Decrease Insider Risk with Effective Security Awareness Training. Security Awareness Training , 1-12.
- Von Solms, R., & Van Niekerk, J. (2018). From information security to cyber security. Computers and Security, 38, 97-102.
- Walumbe, D., Ogalo, J., & Wasike, J. (2019). The Security Mechanisms Put in Place against Insider Information Systems Security Threat in Public Universities in Kenya. The International Journal Of Science & Technoledge, 5(6), 50-56.
- Wapukha, W. D. (2020). An Update To The Insider System Security Attack Prediction Model To Suit Selected Public Universities In Kenya. Kisii: Thesis, School of Information Science and Technology, Kisii University.
- Warkentin, M., & Willison, R. (2020). Cost of Insider Threats Global Report, Observer IT. Michigan: Ponemon Institute.