Submission to VIJ 2024-02-14
Keywords
- Auto encryption; Cloud Computing; Security; Cloud Service Pro- viders.
Copyright (c) 2024 Mst Zannatun Ferdus, Mst Zannatun Ferdus, Md. Hasan Monsur, Mst. Jahanara Akhtar, Saiful Islam

This work is licensed under a Creative Commons Attribution 4.0 International License.
Abstract
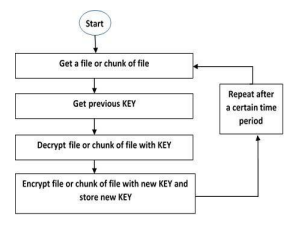
In the IT sector, cloud computing is a rapidly expanding technology. Users are being offered more and more flexible and appropriate services by cloud service providers (CSP). Cloud computing users are increasing at a steady pace. Users and CSP are looking for appropriate security measures as cloud computing becomes a need in modern life. A large number of researchers are studying cloud computing security issues. This work introduces an appropriate cryptography and secure user authentication system, which includes auto encryption and a mechanism for updating keys on a cloud site that is not initially accessible to users. After a predetermined amount of time, this operation will recur frequently on the cloud site. This protocol can be carried out manually by CSP at any time, or it can run automatically after a predetermined amount of time. This will guarantee additional data security. Additionally, this procedure adds a level to the user's credentials. Even with legitimate credentials, these feathers will ensure that hackers cannot obtain original files or data. The suggested protocol is emulated by CloudSim, and we saw that there is an additional step requiring user credentials, requiring some time to access files or data for the first time. Although this small amount of time is insignificant and can be disregarded, it significantly improves security.
References
- Subashini, Subashini, and Veeraruna Kavitha. "A survey on securityissues in service deliv- ery models of cloud computing." Journal ofnetwork and computer applications 34.1 ; 1-11, 2011
- Pawar, Pramod S., et al. "Security-as-a-service in multi-cloud andfederated cloud environ- ments." IFIP International Conference on TrustManagement. Springer International Publish- ing, 2015
- Nair, Nikhitha K., K. S. Navin, and Soya Chandra. "Digital Signatureand Advanced Encryp- tion Standard for Enhancing Data Security andAuthentication in Cloud Computing.", 2015.
- Wang, Cong, et al. "Privacy-preserving public auditing for data storagesecurity in cloud computing." INFOCOM, 2010 Proceedings IEEE. Ieee,2010.
- Hendre, Amit, and Karuna Pande Joshi. "A semantic approach to cloudsecurity and compli- ance." 2015 IEEE 8th International Conference onCloud Computing. IEEE, 2015.
- Khanna, Abhirup. "RAS: A novel approach for dynamic resource allocation." Next Gener- ation Computing Technologies (NGCT), 2015 1st International Conference on. IEEE, 2015.
- Huang, Wei, et al. "The State of Public Infrastructure-as-a-Service Cloud Security." ACM Computing Surveys (CSUR) 47.4 (2015): 68..
- Aich, Asish, Alo Sen, and Satya Ranjan Dash. "A Survey on Cloud Environment Security Risk and Remedy." Computational Intelligencea nd Networks (CINE), 2015 International Conference on. IEEE, 2015
- Singh, Aarti, and Manisha Malhotra. "Security Concerns at Various Levels of Cloud Com- puting Paradigm: A Review." International Journal of Computer Networks and Applications 2.2 (2015): 41-45.
- A. Akshay et. al, “Cloud Security Ecosystem for Data Security and Privacy”, 2017 7th In- ternational Conference on Cloud Computing, Data Science & Engineering – Confluence, pp. 288-292, 2015.
- S. Islam, MJ Aktear, MT Islam, MNS Khan “File Encryption Using Clustering Technique in Cloud Computing”, International Journal of Interdisciplinary Innovative Research &Development (IJIIRD), Vol-4, Issue-01,pp. 75-80, 2019.
- S. Islam, M. N. Islam Khan, M. Zannatun Ferdus, S. J. Islam and M. Abul Kashem, "Improving Throughput using Cooperating TDMA Scheduling of Wireless Sensor Networks," 2020 International Conference on Computing and Information Technology (ICCIT-1441), Tabuk, Saudi Arabia, 2020, pp. 1-4, doi: 10.1109/ICCIT-144147971.2020.9213713.
- S. J. Islam, S. Islam, M. Z. Ferdus, M. N. Islam Khan, M. A. Kashem and M. S. Islam, "Load Compactness and Recognizing Area Aware Cluster Head Selection of Wireless Sensor Networks," 2020 International Conference on Computing and Information Technology (ICCIT-1441), Tabuk, Saudi Arabia, 2020, pp. 1-4, doi: 10.1109/ICCIT-144147971.2020.9213750.
- M. Z. Ferdus, S. Islam and M. A. Kashem, "An Innovative Load Balancing Cluster Composition of Wireless Sensor Networks," 2019 Global Conference for Advancement in Technology (GCAT), Bangalore, India, 2019, pp. 1-4, doi: 10.1109/GCAT47503.2019.8978385.
- M. Z. Ferdus, M. Nurul Islam Khan, S. Islam and M. A. Kashem, "VFLT: SQA Model for Cyber Physical System," 2019 Global Conference for Advancement in Technology (GCAT), Bangalore, India, 2019, pp. 1-4, doi: 10.1109/GCAT47503.2019.8978289.
- MS Bhuiyan et al. “Advancements in Early Detection of Lung Cancer in Public Health: A Comprehensive Study Utilizing Machine Learning Algorithms and Predictive Models” Journal of Computer Science and Technology Studies, Vol. 6, issue 1, pp 113-121, 2024.
- P. K. Das, M. Abul Kashem, Z. Ferdus and S. Islam, "Development and application of a new computerized smell generating system," 2019 Global Conference for Advancement in Technology (GCAT), Bangalore, India, 2019, pp. 1-5, doi: 10.1109/GCAT47503.2019.8978397.